Many people have asked me in the past to explain how in the world I handle so much E-Mail. Since it’s such a long story consisting of many parts, I rarely answer it. Also because I think it’s easier to describe using diagrams, examples and sciency looking graphs. In fact, it turns out, that even describing how much mail I get, and why I get so much, is a story in itself. So this is part #1 of like 2 that describe my E-Mail setup. This first part consists entirely of a description of how much mail I get in the first place. Believe you me, it’s quite a bit.
So, how much raw E-Mail do I get?
So before this, I actually wasn’t even sure. It turns out that the answer is simply put as “a lot”. A whole heaping lot. Much of it is, of course, spam (I don’t have an exact percentage at the top of the article). But even assuming that it’s 90% spam, which likely isn’t the case, I still receive a lot of mail. And it’s all my fault because, simply put again, I want that much (gasp). Ok, maybe not the spam.
So let’s start off with some (sciency) graphs showing the raw numbers of E-Mail that I attract. To really understand it all, I need to break it down into chunks and study each piece.
The Long Haul: Mail Per Month
The first graph below shows the amount of mail per month that I received over the last year-ish.
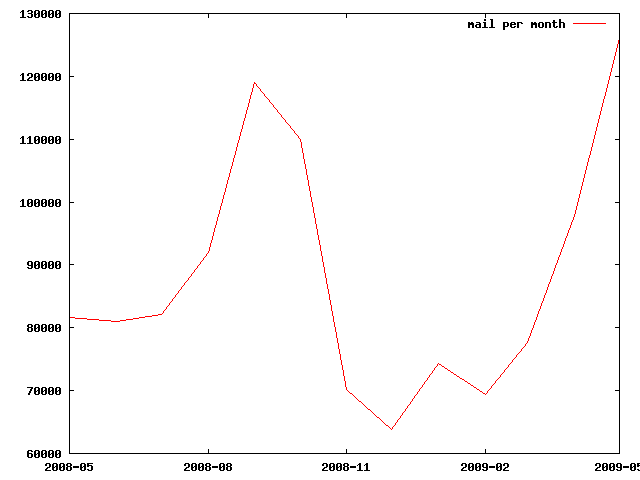
Mail Per Month
The important thing to notice in the above graph is that the amount of mail I receive isn’t even consistent month to month as it ranges from 6500 in a month to almost 13,000. Sure, February has less days in it so you’d expect it to be lower because all months were not actually created equal. But even those slight variations don’t account for the huge swing in differences from month-to-month. Some of it certainly is because my work-load with respect to communication comes and goes. Some months I simple receive a lot more mail for work related projects than other months (usually as deadlines approach and panic ensues).
But the biggest reason for the fluctuation is that spam comes in waves too. Just looking at my day to day E-Mail it’s always amazing how much the incoming spam varies. Some of my email addresses (I have many) are widely published and thus widely harvested by the evil address-collecting spam machines. This results in a huge amount of my mail being spam, unfortunately.
But beyond that, you can see trends in the graph where, for a while, there was a significant drop in incoming E-Mail. This was because a major spam ring was taken out of service a while back and that’s where the huge dip comes from (you should have had a spam dip in that time frame too). However things are unfortunately back to spam-normal again. Do you feel like all of a sudden you’re getting more spam than you used to? Well, you’re not alone. Eventually the next spam king-pin took over and we’re back to an abysmal spam rating of something like 90% on-average spam. The peace was nice while it lasted, but now I’m back to evaluating whether my rich Nigerian uncle really did leave me a fortune or not. Fortunately if he didn’t, it turns out I have 1094 other rich Nigerian uncles who also amassed a small fortune if only I could pay the wire-transfer fee to get it safely into my bank account.
The Shorter Haul: Mail Per Day
The next graph shows the amount of mail per-day that I received mostly during the month of May (2009).
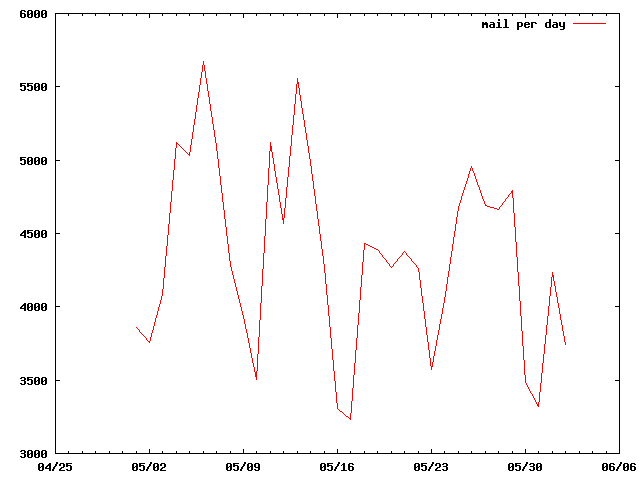
Mail Per Day
There are a couple of interesting actifacts that you can hopefully spot in this graph as well. You’ll notice that has a definite repeating cycle. The cycle is simply this: the low spots are on the weekends. I.E., by far the most mail I receive comes during the work week. This isn’t surprising to me since much of the mail I receive is work related in the first place. Which begins to tell you how much mail I receive for work-related purposes.
Ok, But What Exactly Is It All Then?
There’s the real question. If I get bombarded with so much mail, how much do I actually read??? So, lets pick a day. Ok, let me pick a day since you couldn’t help me there. I picked June 3rd, 2009 which is a Wednesday.
On Wednesday June 3rd, 2009 I received 4514 individual pieces of email. Now, lets quickly do the math shall we? If I tried to read all of that and I did so in, say, a 10-hour period (8 hours for work and 2 hours of reading just the personal mail) that would be 4514/(60*10) = 7.523 email messages per minute that I would have had to read. Though that might be possible if they were all short, I assure you that the people I correspond with are not well known for writing short, brief messages. Long winded rants are, unfortunately, much more common.
Weeding Out The Spam And Rich Uncles
So, the first thing we need to do is remove the auto-discarded spam and duplicate messages (I have a nice filter that removes duplicates so that I’m never bothered twice because someone put me on both the To and the CC line or because I’m subscribed to multiple mailing lists that the message went through). It turns out that in the 4514 messages, I auto-discarded 3163 of them. That’s roughly 70% of them. Since that’s most likely spam, that’s probably close to the real spam percentage that I receive: 70%.
Looking At What’s Left
That leaves only 4514 – 3163 = 1351 messages left to handle. And if I had 10 hours to sift through 1351 messages in my INBOX I could do so at the leisurely rate of 2.25 messages per minute. That’s almost doable (at least if I blacklist a few of the people that mail me the most long of the long winded rants).
But here’s the real secret. Of all those 1351 messages, only 10 actually ended up in my INBOX. That’s important, so let me repeat it. In bold. Only 10 messages actually ended up in my INBOX. And there’s the secret to my success: everything else gets filtered out and placed somewhere else. In fact, if you really look at how I treat mail it turns out I have lots of INBOXes. The one that only received 10 is the one that is just mail sent to my personal account. My work addresses only received 16 to the work INBOX equivalents.
Dealing With Mail in Clumps
So what is really happening, behind the scenes, is that my mail for the day actually got sorted into 44 different places. Not just 1 or 2, but 44. That lets me sort and prioritize my mail so that the important stuff I can see right away in small INBOXes and they don’t get lost in the bulk of the rants.
In the rest of the mail: 638 messages went to a folder for fedora developers consisting of auto-generated emails describing upcoming changes to the operating system. Another 110 were long winded rants about the same operating system that went to a discussion folder (at least I bet they were long winded rants; I didn’t study most of them in detail). 102 were about my favorite linux-based TV recording software: MythTV. Another 120 E-Mails were messages that were most likely spam but placed in a folder for me to double check them because the spam-filtering software wasn’t confident enough to just throw them away without my help.
And so on. You don’t want more of a breakdown than that. Trust me.
Thank You For Waiting;
You’re Message Important To Us Me
That being said even my real INBOX occasionally turns into a black tar-pit where it seems I can never stay afloat. Even with only 10 messages going into it for a particular Wednesday I’m not perfect and frequently I “mean to respond later” but fail to get back to it in a timely manner.
The important thing is that the people that really matter (you) do end up in my highest priority folder (assuming you’re not one of those long-winded ranting folks). Everyone should filter their mail to put their most important email messages first in their lives and let the others stew until they’re nice as savory. I’m going to come back at some point in the not too distant future (I hope) to provide additional guidance for “getting ahead of your email”.
I’ve actually learned something from this long winded analysis too. So I’m glad I wrote it up. What I’ve learned is that I should have a severe headache and should step quietly away from the computer. So I think I will.

 So today (June 8th, 2011), is the first
So today (June 8th, 2011), is the first